What issue can we solve for you?
Type in your prompt above or try one of these suggestions
Suggested Prompt



Solutions
Fortifying Cloud Security: The Power of Zero Trust
Fortifying Cloud Security: The Power of Zero Trust
No matter what the industry—finance, energy, healthcare, technology—no business is immune from cyber attacks. This precarious climate makes security more important than ever, especially in today’s cloud landscape. Cyber threats are always increasing in sophistication, and so must the solutions for combating them.
Implementing security across the cloud enterprise can help to mitigate risks, prevent threats, protect data and enable visibility into data and applications. And having a proactive security posture—rather than reactive—can position businesses to stay ahead of cyber attacks and be more resilient when they occur.
But while the importance of security is at a high point, the preparedness of most organizations is low. Many businesses continue to safeguard their IT in silos. They also lack the necessary expertise to protect the enterprise beyond data center security.
Given the scope of risk, organizations must address cloud security more comprehensively. Business leaders should take steps now to secure the cloud environment and be ready for all that may come. This is where zero trust makes a difference.

Ready to take your cloud journey to the next level?
Head over to our dedicated cloud modernization landing page to chart your modernization journey.
A new ally: Zero trust
Zero trust in the simplest of terms means trust nothing. The core principle of this security framework centers on never trusting and always verifying—assuming that the network is always at risk of internal and external threats. Zero trust complements and enhances the capabilities of cybersecurity technologies like SIEM, SOAR, CSPM and CNAPP by providing a strategic framework for enforcing strict access controls, continuous monitoring and least privilege principles across the entire IT environment. Continuous verification elevates a business’s security posture as it aligns with the dynamic nature of cloud environments.
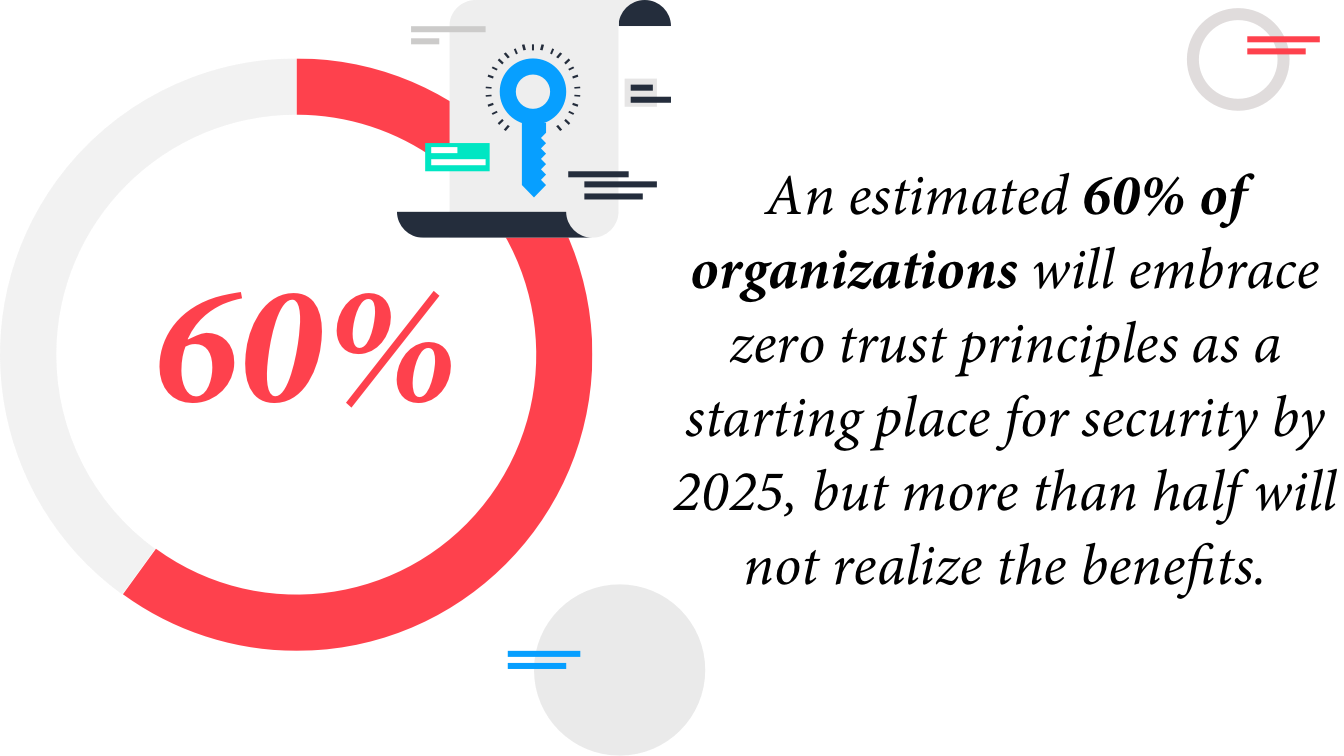
Gartner estimates that more than 60 percent of organizations will embrace zero trust principles as a starting place for security by 2025, but more than half will not realize the benefits.1 They also predict that by 2026, 10 percent of large enterprises will have a mature and measurable zero-trust program in place. That is a leap from less than 1 percent today.2
Developing security strategies that align with the dynamic nature of cloud environments can help organizations enhance compliance, control and resilience. Because most organizations don’t have the in-house expertise to adopt leading-edge cyber security, it is critical to find a partner who can.
Strength in security
Publicis Sapient works with clients to break down security silos by implementing an integrated security strategy that ensures seamless collaboration and a unified defense against evolving threats. Our teams have the cloud, zero trust, security and integration expertise required to seamlessly unify cloud applications and security tools to ensure security does not compromise operations. We embed zero trust principles to build the resilient security posture that is needed for dynamic cloud environments.
We partner to empower organizations to proactively identify and address threats, safeguarding the confidentiality, integrity and availability of critical assets. Our team includes more than 700 cloud security specialists with over 2,000 certifications. Clients gain peace of mind knowing that we bring in-depth experience transitioning organizations from cumbersome firewalls to agile, software-defined and robust security solutions.
As a result of our collaboration, our clients achieve outcomes that include:
-
Improved monitoring and alerting
![]()
Enhanced compliance and risk reduction
![]()
Better visibility and control
![]()
Heightened speed and agility

Reduced operational cost
One example is our work with ADQ, an Abu Dhabi-based investment holding company, where we implemented “always-on” security through a cloud-native centralized solution for threat detection, proactive threat hunting and automated threat response. The platform monitors analytics for workload protection, security posture management, vulnerability management, secure data, compute and infrastructure, leveraging advanced threat intelligence to triage and prioritize threat events, reducing alert fatigue. ADQ gained visibility, definition, consistent application and measurement of security goals across a distributed and diverse set of technologies.
Protect your enterprise
Don’t run the risk of falling behind in addressing security concerns and mitigating risks. Stay ahead of the curve by utilizing zero trust principles and implementing cloud security that keeps your security posture adaptive and resilient. When your business can better monitor and assess security risks, it can fearlessly achieve its business goals.

Ready to take your cloud journey to the next level?
Head over to our dedicated cloud modernization landing page to unlock the full potential of cloud for your organization with downloadable resources.
For more information on our holistic Cloud and Infrastructure Solutions, let’s connect:
Related reading
-
![dollar sign suspended in the clouds]()
Say Goodbye to Cloud Sticker Shock, with FinOps
Embrace cloud-native security practices and zero trust principles to align your security framework with the dynamic nature of cloud environments.
-
![white and blue geometric-shaped clouds on top of a tablet screen]()
Cloud & Infrastructure Solutions
Rely on end-to-end integration services to define the strategy, platform and architecture necessary for seamless, scalable and secure cloud migration.
-
![icons of computer screen with padlocks in clouds and arrows indicating data being shared two ways]()
How to have an overarching effective position on security
With more technology and innovation, comes greater risk to security.










